Implementing Cross -Site Request Forgery Protection in Web application using Synchronize Token
Cross-Site Request Forgery (CSRF), also known as Session Riding and XSRF, is a common application-layer vulnerability that allows the malicious attacker to use an active session of the victim to perform actions on his behalf without his prior knowledge or consent. CSRF incidents are hard to detect as they are disguised into normal user requests.[checkmarx]
Today I am going to show how to secure login using tokens.It's basically about confirm login using CSRF token.
First we have to implement index.php [client side] and create a cookie to store session id(this cookie will be useful in later, when we validate the session id in the server side)
Then we have to generateCSRF token and store it in the server side(server.php).
Now we have successfully generated our CSRF token in server side.Next we have make a request to the server when client page is loaded and get the CSRF token which was stored in the server side.In order to do that we are using AJAX along with the Javascript.
I create a function called "loadDOC" . The function will request to the server side and grab CSRF token and store it in the "hidden" DOM field in the client side when the page is loaded.
Calling the loadDoc function in the client side.
After that we need to create the hidden DOM field to store the CSRF token value.This value should send to the server side again when user try to login.
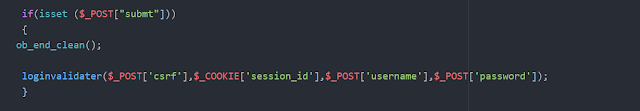
when the user try to login all the values in the form will redirected to the server.php. After that we need to validate those received values in server side
Here i have implement loginvalidator function which verify the user credientials.The hash_equals function compares two strings using the same time whether they're equal or not.So using this function we can simply verify the CSRF token.
When the user try to login , it will automatically call the function and if the token matches the login will be successful otherwise it will show an error message.
For Source code
Click here








Comments
Post a Comment